Research groups and members of staff working with sensitive data can encrypt their data using Symantec File Share Encryption. Symantec File Share Encryption works by installing itself as part of the Windows Operating System and for the most part, it works transparently to the user. Encrypted files and folders are encrypted and decrypted without you even noticing. Anyone with access to the file system, but who is not part of the encryption group and/or does not have the Symantec Encryption Desktop client installed, won't be able to access or read the files or folders.
Note: This service is only available for Windows users. Please note that Symantec is not compatible with Microsoft OneDrive for Business, as files can get decrypted when they are synced to the cloud and/or will report incorrect encryption status/properties.
If you decide to use this service, ICT will need to set up a few things first.
- ICT will create you a new group (or use an existing group if you have one already) that is used for encryption purposes
- ICT will also need to install the Symantec Encryption Desktop client on the PC/laptop of everyone that is going to use the service
Once set up, you will need to decide on a folder within your network shares that you designate as an encrypted folder (should you want to keep encrypted and non-encrypted folders separate). It is possible to create more than one encrypted folder, but this might increase the management overhead of your encrypted (and non-encrypted) filing system. Please contact the ICT Service Desk to get this set up.
FAQs
- How do I set up an encrypted folder?
- What different rights and permissions do the different roles (admin, group admin or user) have?
- I added my colleague to the encryption group, how come they still cannot decrypt the files/folders?
- Why do I see PGPFS.INI files in the root of every encrypted folder?
- How can I immediately tell if a folder is encrypted or not?
- What happens if I take an unencrypted file/folder and move it to an encrypted folder?
- What happens if I take an encrypted file/folder and move it to an unencrypted folder?
- How can I decrypt a file or folder to share with someone who is not part of my encryption group and is not using Symantec Encryption Desktop?
- I am in the right encryption group, and I have Symantec Encryption Desktop installed, why don’t I have rights to decrypt a file or folder?
- My Symantec Encryption Desktop client is asking me for a passphrase and/or something is not right, what can I do?
- My Symantec Encryption Desktop client is still not right and updating the policy has not fixed it, what can I do?
- Why are my files are corrupt/unreadable?
- How can I see the various Symantec File Share Encryption settings and permissions on my encrypted folder(s)?
- How can I see the various Symantec File Share Encryption settings and permissions across multiple encrypted folders?
- User guides
To start using Symantec File Share Encryption, you will need to set up an encrypted folder. To do this, follow these steps or contact the ICT Service Desk for more assistance.
- Right-click the folder you want to encrypt and choose from the context menu: Symantec Encryption Desktop > Encrypt “<folder name here>” with Symantec File Share…Advanced.
- In the new dialogue box (Add Users) that appears, click the Add button.
- In the new dialogue box (User Selection) that appears, click ‘icsecsem.cc.ic.ac.uk’ and then search for your encryption group by typing the first few characters of the group's name in the search box and pressing the search icon (magnifying glass).
- Highlight your group on the left-hand side column and click Add (bottom left corner) to move your group into the right-hand side column and click OK.
- In the previous dialogue box (from 2. earlier), right-click your group name and make your group one of the following roles and then click Next:
- Admin (has full control over encryption groups)
- Group Admin (has limited control over encryption groups)
- User (has no control over encryption groups)
A comprehensive description of these three roles and their associated permissions and rights can be found in the FAQ below.
6. Choose a signer from the drop-down list (it will most likely be your name) and click Next.
7. This is the last dialogue box. Depending on the size of your folder and/or how many files/sub-folders you have, this might take some time. When it has been completed, click Finish to close the dialogue box.
Admin
This is the "owner" of the protected folder. The Admin can add users and remove users, and can change the roles of Users and Group Admins. The Admin has full rights to read and write to the protected folder. There can be only one
Admin for each protected folder and it is created automatically by the creator — you do not need to specify an Admin manually for the protected folder. There is only one Admin per folder.
You become an Admin by creating a protected folder, adding yourself as a member, and applying the Admin role to yourself. You can be a member of multiple Admin sets at one time.
The Admin role cannot be removed by a Group Admin, but an Admin can reassign their role to another member.
Admins must have full write access to the protected folder.
Group Admin
This is an "administrator" of the protected folder. The Group Admin can add and remove users, and can promote users to Group Admins or demote Group Admins to Users. There can be as many Group Admins as needed.
The Group Admin has full rights to read and write to the protected folder. There can be multiple Group Admins for each Symantec File Share Encryption protected folder.
Group Admins must have full write access to the protected folder.
Users
This is the set of users who are allowed to access the protected files in the shared space. The files in the protected folder are encrypted to the keys of the Users.
You become a User when a protected folder is created, you are added to the Symantec File Share Encryption, and the Admin or Group Admin assigns the User role to you. All Users have equal privileges to read and write to the protected
folder. Users do not have the ability to change the roles of other Users.
You can be a member of multiple User sets at one time. Users do not have the right to decrypt files or folders. This is limited, so Users cannot decrypt files and re-encrypt the files with new role assignments.
This all depends on when the person was added to the group. Group membership usually takes about an hour to synchronise over to the Symantec Encryption Server. However, on some occasions, this can take up to 6 hours. Unfortunately, this sync time constraint is beyond ICT’s control.
These system files will only be visible by users with access to the files and folders, but do not have the Symantec Encryption Desktop client installed.
If you have the Symantec Encryption Desktop client installed, encrypted files and folders will have a blue padlock icon displayed in the bottom left-hand corner of the icon.

Note: Unfortunately, sometimes, this blue padlock icon does not always get displayed and this can usually be fixed by refreshing your Windows Explorer window by pressing the ‘refresh’ icon or pressing F5
If you do not have the Symantec Encryption Desktop client installed, encrypted folders will be identifiable as folders with PGPFS.INI file within it.

If you have SED installed, and you move (or copy) an unencrypted file or folder to an encrypted folder, that file or folder (and its contents) will automatically become encrypted to the same settings/groups as its parent folder.
If you have SED installed, and you move (or copy) an encrypted file or folder out of an encrypted folder, that file or folder (and its contents) will remain in its encrypted state.
Firstly, using Microsoft Outlook, if you attach an encrypted file/document(s) to an email, that file/document(s) will be automatically decrypted ‘on the fly’, so there is nothing extra the user must do in this respect.
If you want to share a document with a user who is not part of the encryption group, yet you have a common file share/folder that you both use outside of the encrypted folder system, then simply copy (or move) the file/folder to the shared area and decrypt it. To decrypt the file/folder, right-click and from the context menu choose:
- Symantec Encryption Desktop>
- Decrypt “<insert file/folder name here>” with Symantec File Share
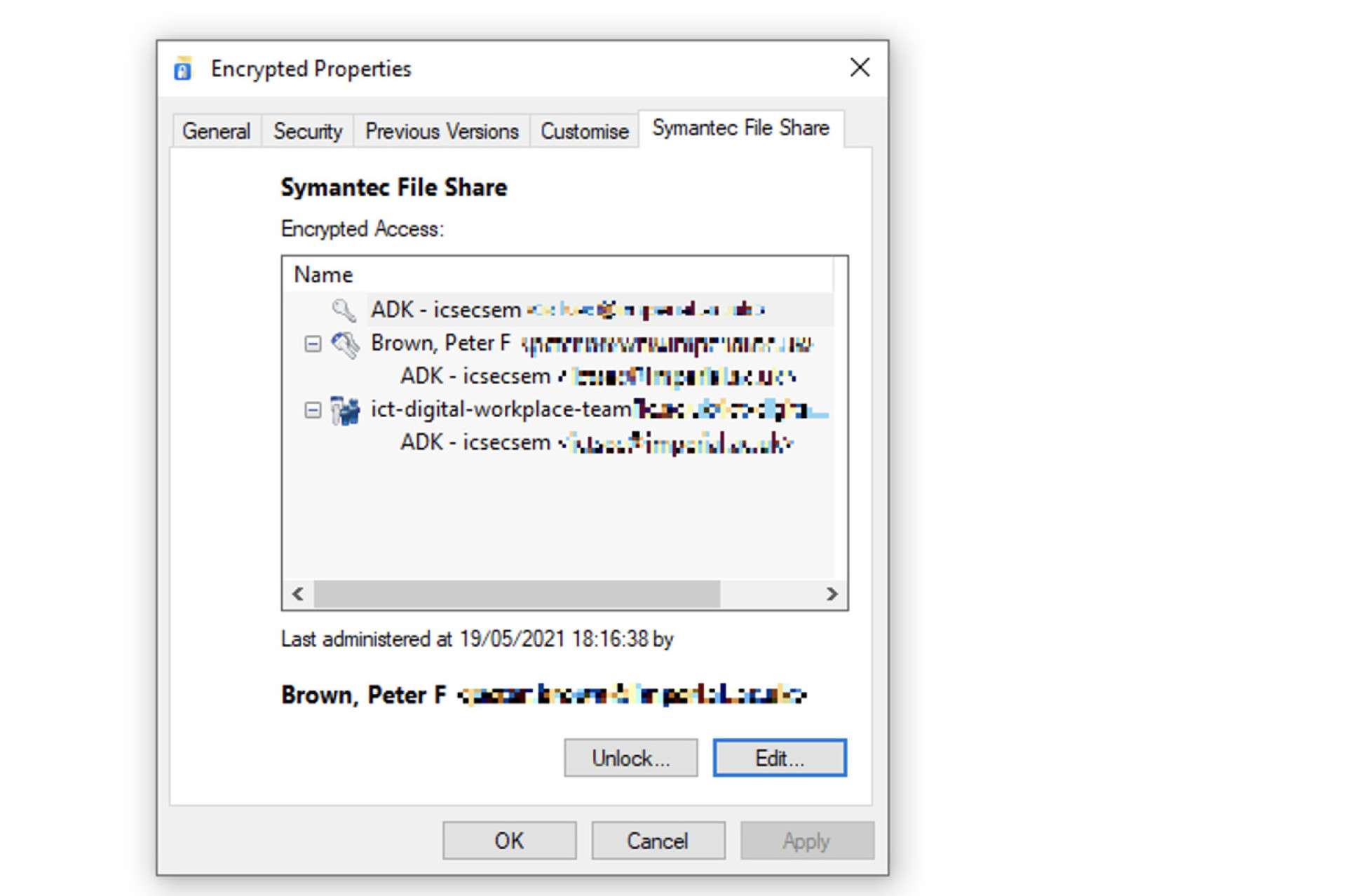
There may be occasions where you cannot access encrypted files or folders, despite being in all the right groups and having Symantec Encryption Desktop installed. This is often because the file or folder has had the parent folder’s group key removed and has been encrypted with either a single users key or another group’s key. (see illustration below)

If this happens, you will need to contact the ICT Service Desk who will then determine rightful ownership of the data, and if applicable, use the Additional Decryption Key (ADK) to realign the encryption settings and make the file/folder accessible again within the parent group/folder structure.
The Symantec Encryption Desktop client works by synchronising your private keys (which are secured on the Symantec Encryption Management Server) to your local PC/laptop. Sometimes, these keys can either get corrupt or get out of sync. If this error occurs or something is not working how you expect it to, the most common solution is to update the Symantec Encryption Desktop client policy.
To do this, right-click the Symantec Encryption Desktop system tray icon and choose ‘Update Policy’.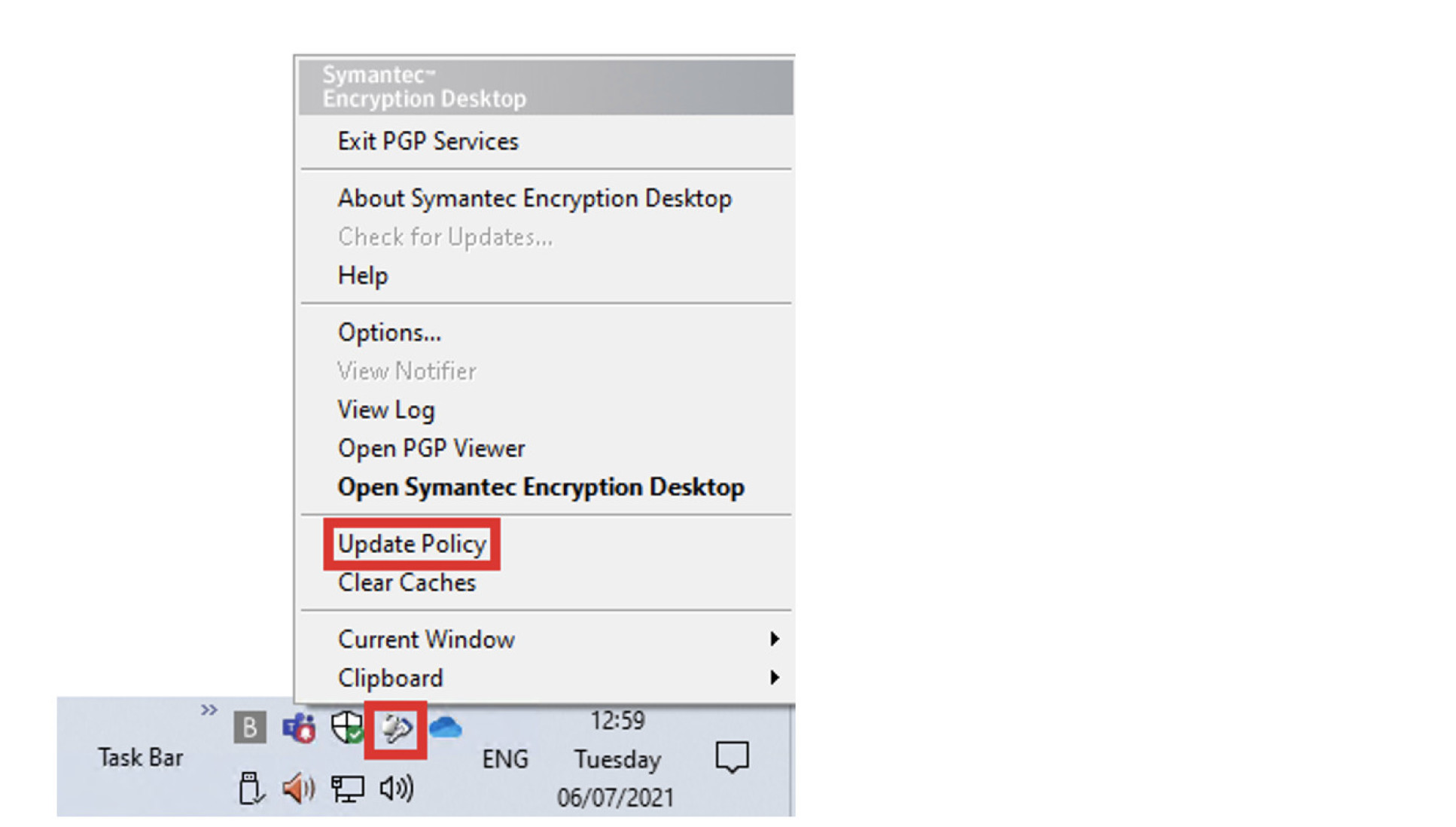
In rare cases, the Symantec Encryption Desktop client installation itself can become corrupt and you can get all manner of errors ranging from ‘Contact your Administrator’ or ‘This file is corrupt’. When this happens, it is possible to reset your SED client completely and start afresh. To do this, either contact the ICT Service Desk for assistance or if you feel comfortable enough, you can reset the client yourself by performing the following:
- Close the SED client completely by right-clicking the system tray icon and choosing ‘Exit PGP Services’
- Click ‘OK’ to the warning message
- Press the Windows key (on your keyboard) together with the letter ‘R’ and in the dialogue box that pops up enter ‘%appdata%’ (without quotes) and press ‘OK’
- In the new explorer window that pops up, navigate into the ‘PGP Corporation’ folder
- Copy (or move) the ‘PGP’ folder to a safe location (this is just a precaution in case there are keys in there that do not exist on the server, but this is extremely rare)
- Now delete the ‘PGP’ folder completely and close this window
- From your Windows Start menu, find and start Symantec Encryption Desktop
- You will now be required to enrol and trust the Symantec Encryption Management server certificate and enter your college username and password again
- Symantec Encryption Desktop should now be performing as expected
If your documents look like this (see illustration below), you are most likely using a PC or laptop that does not have Symantec Encryption Desktop installed. This can arise if you have had to switch from your regular PC or laptop to a temporary one.
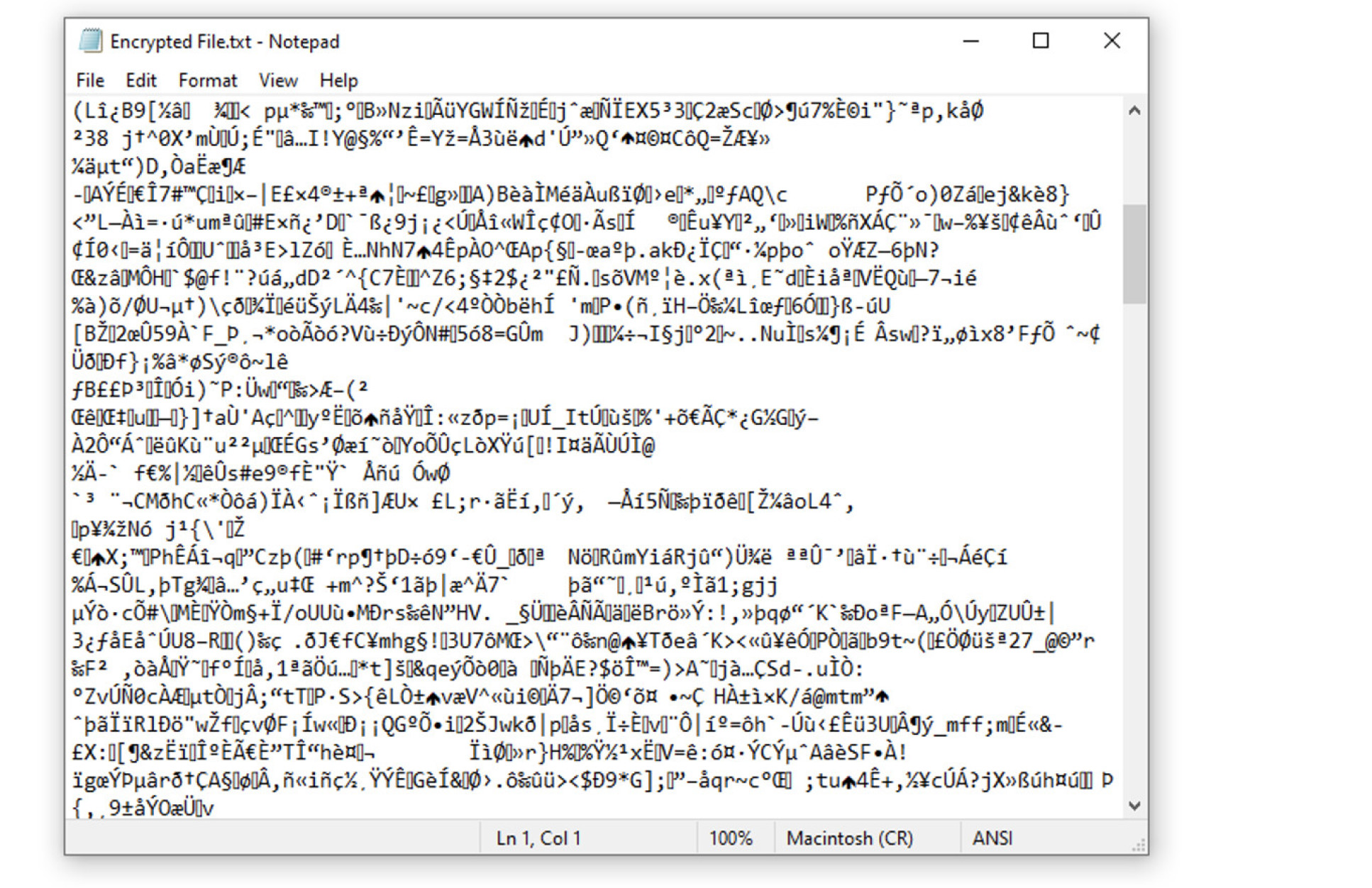
In this scenario, contact the ICT Service Desk to have Symantec Desktop Encryption installed on your temporary device.
Right-click the file or folder in question and choose the Symantec File Share tab
For more advanced usage, Symantec provides a command-line tool (pgpnetshare.exe) bundled with the Symantec Encryption Desktop client. With some Windows command line or PowerShell scripting, it is possible to report on multiple folders across your network shares or file system, as well as other encryption/decryption tasks.
For more information on what this command-line tool can offer and how to use it, please refer to the documentation/user guide at the bottom of this page or contact the ICT Service Desk. 